Intercept X Advanced consistently rates at the top of independent tests and analyst reports for endpoint protection.
End to End Endpoint Protection
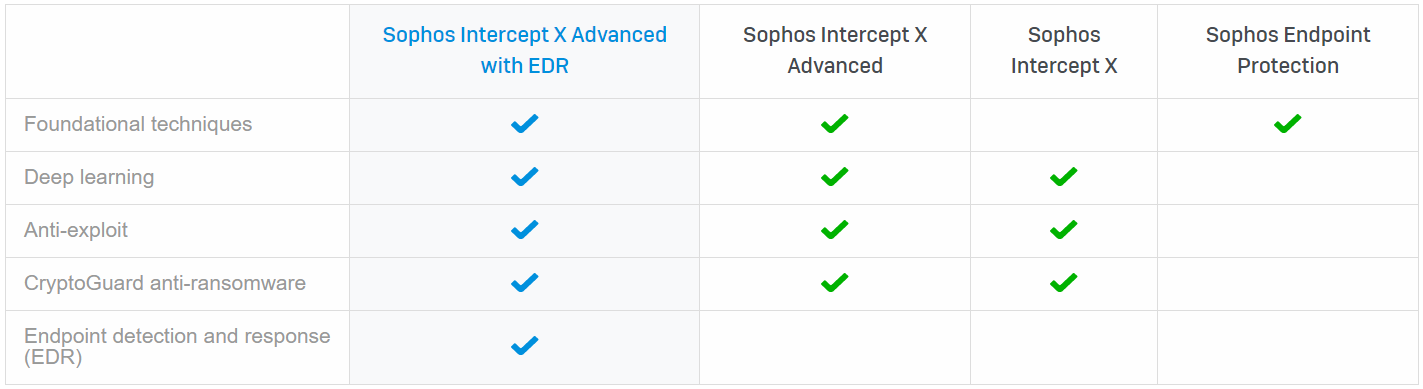
To stop the widest range of threats, Sophos Intercept X employs a comprehensive defense-in-depth approach to endpoint protection rather than simply relying on one primary security technique. This is the “the power of the plus” – a combination of leading foundational (traditional) and modern (next-gen) techniques. Intercept X integrates the industry’s top-rated malware detection and exploit protection with built-in endpoint detection and response (EDR).

Harness the Power of a Deep Learning Neural Network
Drive threat prevention to unmatched levels. The artificial intelligence built into Intercept X is a deep learning neural network, an advanced form of machine learning that detects both known and unknown malware without relying on signatures.
Deep learning makes Intercept X smarter, more scaleable, and higher-performing than endpoint security solutions that use traditional machine learning or signature-based detection alone.

Stop Ransomware
CryptoGuard in Intercept X is the world’s best ransomware protection. It uses behavioral analysis to stop never-before-seen ransomware and boot-record attacks, making it the most advanced anti-ransomware technology available.

Malware Cleanup
Intercept X includes the industry’s most powerful malware cleaner. While most virus cleaners simply remove offending malware files, Sophos Clean provides forensic-level remediation by eradicating malicious code as well as eliminating nasty registry key changes created by malware as well.

Complement Or Replace Your Existing Antivirus
Sophos Intercept X Advanced combines the modern techniques found in Intercept X with the proven foundational techniques found in Sophos Endpoint Protection – all in a single agent. Intercept X can also be used to augment your existing endpoint security or antivirus software, giving you deep learning malware detection, anti-ransomware, anti-exploit technology, root cause analysis, and more.